Getting Hacked Sucks! If you have ever had your website hacked, you know that feeling – the dreaded fear of vulnerability and the humiliation of defeat. In my 20-year career in digital marketing, I have felt that feeling a few times. The funny thing is that the majority of web hacks are not personal. These people do not know you and they do not hate your business – they are simply running automated scripts that scour the internet to find vulnerabilities and exploit them for either bullshit money-making purposes or just plain being assholes.
I was once attacked by a guy who got access to my web file directory and simply pasted text docs in every folder that had the word “HACKED” written on them. That was it, nothing malicious, didn’t wreck any pages or files,… just being a pain in the ass. On another instance, the hacker actually got into the backend of my WordPress site and set it up to redirect anyone visiting my site to be redirected to some Financial Firm in China. That one was fun to troubleshoot and fix.
This entire article to urge you to start paying attention to your website’s vulnerabilities and to ask questions of your web designer.
How a WordPress Site Gets Hacked
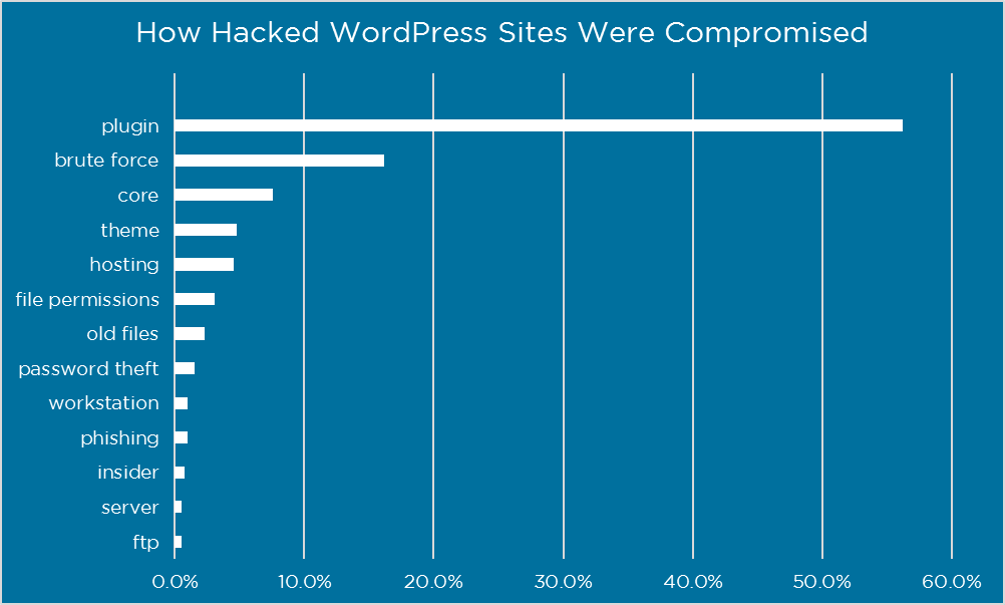
In this post, we’re going to focus primarily on the top two risks – plugins & brute force. Because if you can protect yourself against plugin vulnerabilities and brute force attacks, you are accounting for over 70% of the problem.
Plugins Are Your Biggest Risk
Plugins play a big part in making WordPress as popular as it is today. There are over 50,000 plugins available for download in the official WordPress plugin directory. That is an incredible selection of awesome and creative plug and play software to enhance your website. But you obviously need to be careful with them, as plugin vulnerabilities represented 56% of the known entry points.
Here are some tips choosing plugins and keeping those plugins safe from attacks.
Keep them updated
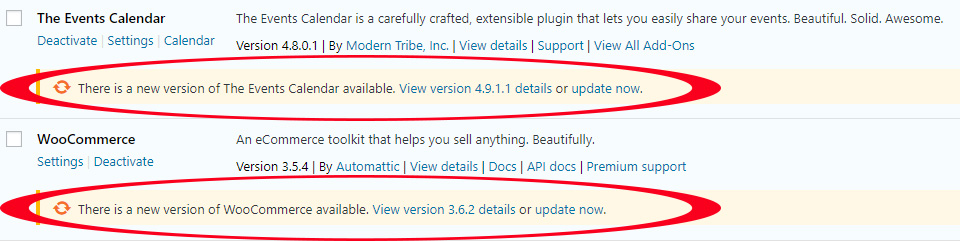
Reputable plugin authors fix vulnerabilities very quickly when discovered. By keeping them up to date you ensure that you benefit from fixes before attackers can exploit them. We recommend that you check for updates at least monthly.
Don’t use abandoned plugins
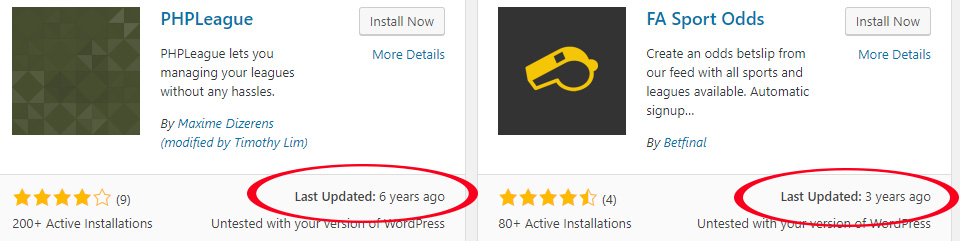
You are relying on the plugin developer to ensure that their code is free of vulnerabilities. If they are no longer providing updates there is a high likelihood that there are vulnerabilities that have not been fixed. We recommend avoiding plugins that have not been updated in over 3 months. For plugins you have already installed we recommend you conduct an audit at least quarterly to make sure none of your plugins have been abandoned by their authors.
Only download plugins from reputable sites
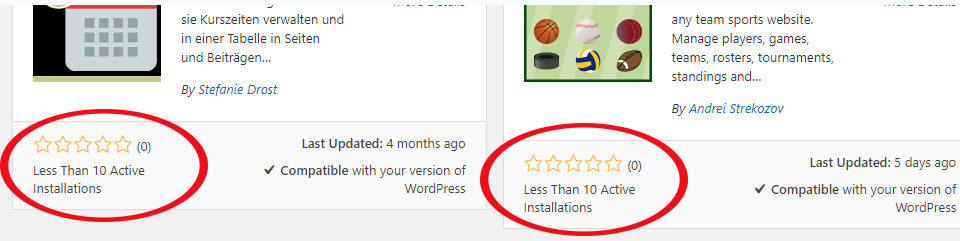
If you are going to download plugins somewhere other than the official WordPress repository, you need to make sure the website is reputable. One of the easiest ways for attackers to compromise your website is to trick you into loading malware yourself. Be sure they have a lot of downloads already, and a good rating.
Brute Force Attacks Are Still A Big Problem
A brute force attack is a password guessing attack. The attacker needs to both identify a valid username on your website and then guess the password for that username. Despite the availability of methods and technology that are 100% effective, this type of attack is still a huge problem, representing 16% of known entry points.
I get these emails on a daily basis from my security software on my client’s sites…

And in my client’s WordPress admin portals, I see data and stats like this every day…
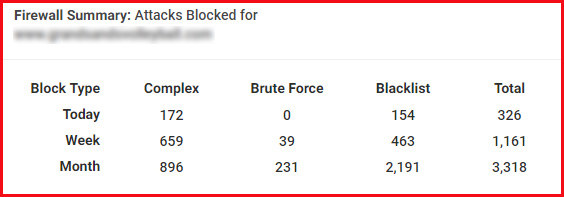
Most of my clients don’t know that their site is being attacked hundreds, if not thousands, of times each month. It’s my job to ensure their site is protected.
Some tips for avoiding a hack via brute force attack:
Use Cellphone Sign-in
Also referred to as two-factor authentication, this approach requires the user to not only know their password, but to have possession of their cell phone as well. This technology is 100% effective in preventing brute force attacks.
Don’t Use Obvious Usernames
The most obvious usernames to avoid are ‘Admin’ and ‘Administrator’, they are the most common usernames attempted in brute force attacks. Also avoid using your domain name, company name and the names of people who are writing for your blog or are listed elsewhere on your website.
Enable Login Security
A fantastic plugin that I use on ALL my sites is Wordfence. It provides a long list of login security features.
- Enforce strong passwords
- Locking users out after a defined number of login failures
- Locking out users after a number of forgot password attempts
- Locking out invalid usernames
- Preventing WordPress from revealing valid usernames in login errors
- Preventing username discovery through author scans
- Immediate blocking of IPs that try to sign in as a defined list of usernames.
Conclusion
WordPress security is a battle fought on many fronts. But knowledge is power. This post is not set up to scare you, just make you aware of the realities of cyber hacking.
I hope that you take the opportunity to make improvements in how you select and manage plugins on your website. We also hope that you review your approach to brute force attack protection. Small investments in these areas will pay big security dividends. Stay safe!
Author
TJ Swing
Founder and President, Zagrun Marketing


